Spyware: What it is and how to protect yourself
Spyware is a type of malicious software that is installed on your computer or mobile device without your consent, and it can gain access to your sensitive personal information and then relay it to other parties, resulting in anything from pesky advertising and pop-ups to tracking your keystrokes and capturing your login credentials. Follow this guide to learn more, including about how Norton 360 Deluxe can help keep your device safer.

What is spyware?
Spyware is a type of malware that's installed on your device without your knowledge or permission, covertly gathering intel about you.
Although the term "spyware" may sound like something right out of a secret agent movie, this sneaky software is anything but entertaining. Spyware is actually one of the most common threats on the internet today. It can easily infiltrate your device and, because of its covert nature, can be hard to detect.
It's worth noting that not all software that tracks your web activity does so for bad reasons. Some online tracking is used for things like remembering your login information or customising your website experience. Spyware, on the other hand, is used with malicious intent.
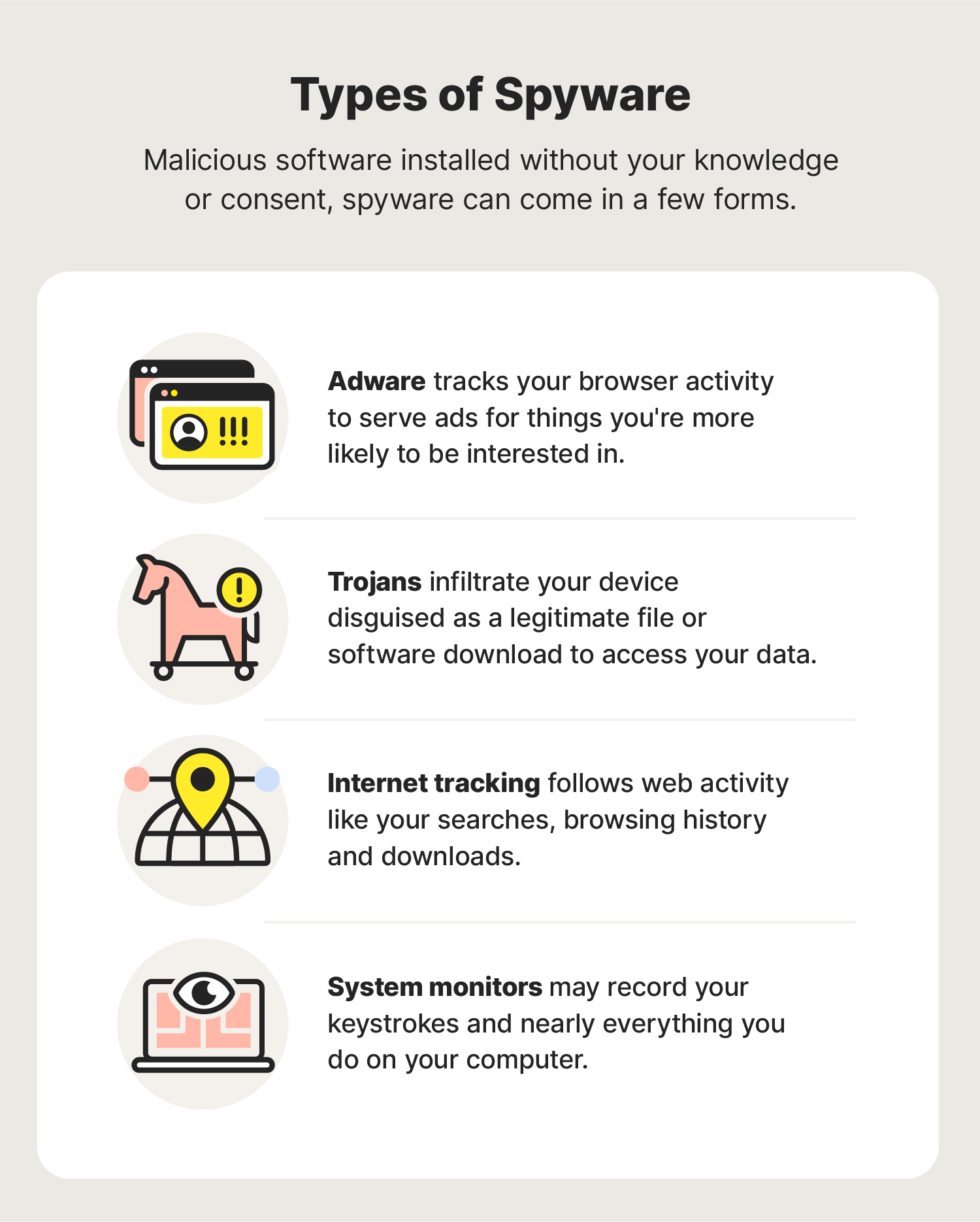
Types of spyware
The four common types of spyware are adware, Trojans, internet tracking, and system monitors. Their function ranges from tracking your browser activity so marketers can target your interests, for instance, to monitoring your keystrokes and nearly everything you do on your device.
Here are some of the unique tactics each type of spyware uses to track you:
- Adware tracks your browser history and downloads with the intent of predicting what products or services you’re interested in. It's used for marketing purposes.
- Trojans are a type of malware disguised as legitimate software. Just like the Trojan horse from Greek mythology, a Trojan tricks you into letting it in (or, more specifically, onto your device), by acting like a benign software update or file. Then it damages, disrupts, or steals your data.
- Internet tracking is a common practice used to follow your web activities—like browsing history and downloads—mostly for marketing purposes.
- System monitors are a type of spyware that can capture just about everything you do on your computer. Keyboard loggers can record all of your keystrokes, emails, chat room conversations, websites visited, and programmes run. System monitors are often disguised as freeware.
How does spyware work?
Just like any other form of malware, spyware infects your device. Here is a breakdown of how spyware works.
- Infiltrates your device: This could happen when you visit a malicious website, unwittingly install a malicious app, or even open a file attachment.
- Captures your data: Once the spyware is on your device, it begins to collect data, which could be anything from your web activity to screen captures to even your keystrokes.
- Provides data to a third party: The captured data is then supplied to the spyware creator, where it is either used directly or sold to third parties.
The data collected through spyware may include things like:
- Web browsing history
- Keyboard strokes
- Email addresses
- Login credentials (usernames and passwords)
- Credit card details and account PINs
Common spyware tactics
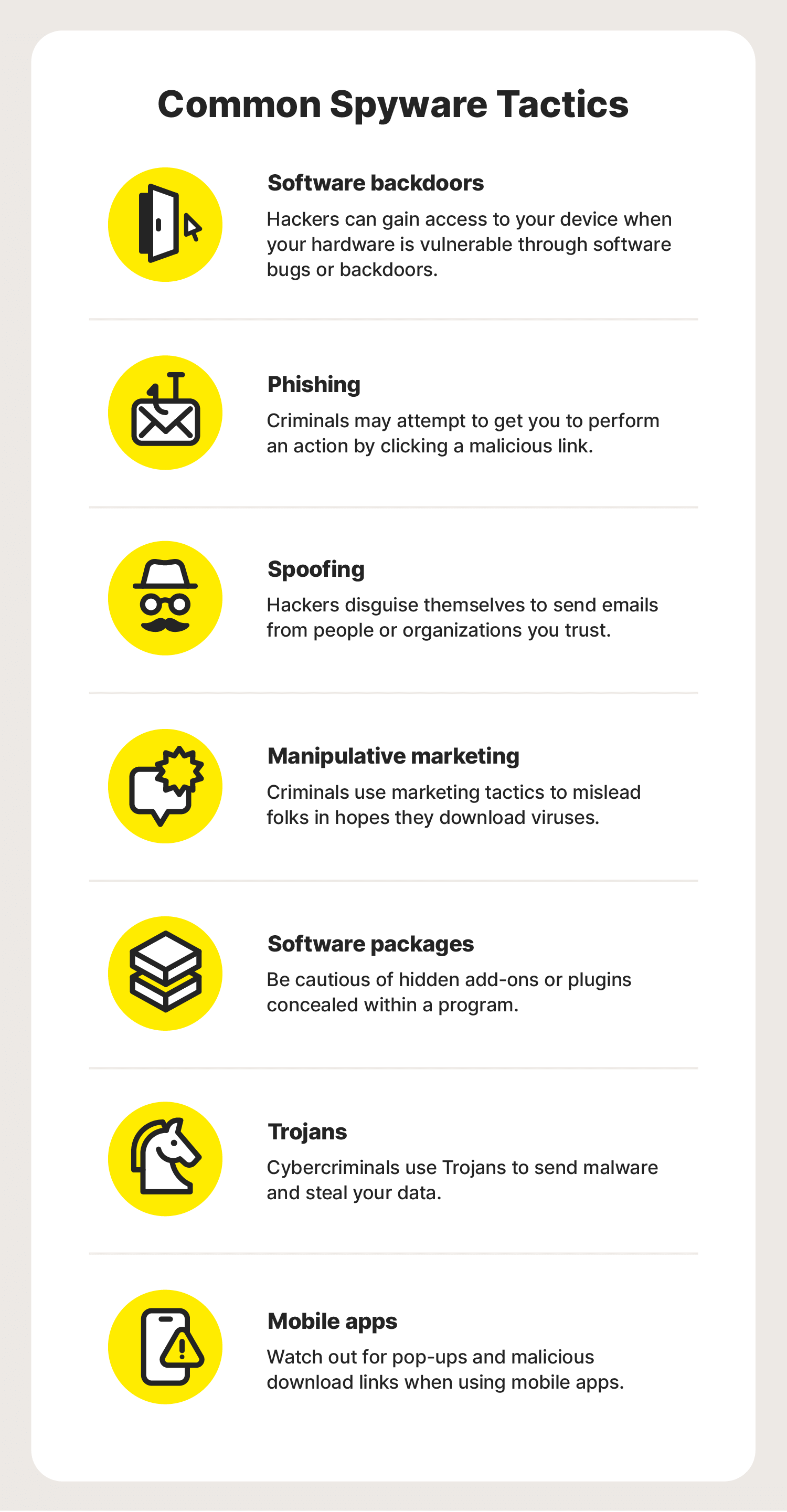
- Software backdoors: Hackers can quickly gain access to your device when your hardware is vulnerable through software bugs or backdoors.
- Phishing: Criminals may attempt to get you to perform an action by clicking a malicious link.
- Spoofing: Some types of hackers disguise themselves to send emails from people or organisations you trust.
- Manipulative marking: Cybercriminals use misleading marketing tactics to promote helpful tools so folks are eager to download them and become a victim of the bait.
- Software packages: Be cautious of hidden add-ons or plugins concealed within a programme.
- Trojans: Cybercriminals use Trojans to send malware and steal your data.
- Mobile apps: Watch out for pop-ups and malicious download links when using mobile apps.
Potential problems caused by spyware
Being a target of spyware can be annoying and even dangerous. Here are some common problems:
- Damage to your device: Spyware can drain the performance of your device, making it run slowly or lag.
- Browsing disruptions: Spyware can alter your device’s settings and search engine results.
- Data theft: Your email accounts, passwords, browsing history, and social network access may be stolen.
- Identity fraud: Cybercriminals can imitate your identity through the personal information they’ve gained.
How to recognise spyware
While spyware was once a more common problem for Windows operating systems, that's no longer strictly the case. Spyware can affect PCs, Macs, and iOS or Android devices, including mobile phones and tablets. Basically, if your device can connect to the internet, it can be infected with spyware.
Some common ways your device might become infected with spyware include:
- Accepting a prompt or pop-up without reading it first
- Downloading software from an unreliable source
- Opening email attachments from unknown senders
- Pirating media such as movies, music, or games
- Clicking a link to a malware-laden website
Spyware creators may use clever tricks to deceive you. The spyware may be packaged alongside free software made to seem like a useful tool, or in an email attachment that seems legitimate.
Signs of a spyware infection
Spyware can be difficult to recognise on your device—it’s meant to be deceptive and hard to find. Like a spy, it works covertly. Even so, there are clues that can help you identify whether you’ve been infected.
You may have a spyware issue if you spot any of these signs:
- Your device is slow, crashes unexpectedly, or starts displaying error messages.
- Your device is running out of hard drive space.
- You're annoyed by frequent and persistent pop-ups.
- Your browser redirects you to pages you haven't navigated to.
- Your browser no longer points to your usual homepage.
- You discover icons for programmes you didn't download on your device.
- Your browser displays a new toolbar or plugin you didn't add.
How to protect yourself from spyware
Spyware creators tend to cast a broad net to gather vast amounts of information from as many people as possible. That's why it's important to take precautions and practice good internet safety.
Although anyone who uses the internet can potentially get spyware on their devices, there are ways to prevent spyware infections.
| Do’s and Don’ts of Minimising Spyware | |
|
|
|
|
|
|
Spyware authors have sophisticated ways of tricking internet users into unwittingly downloading spyware. It pays to treat anything unexpected or unknown that appears on your device or in your email inbox as suspect until proven otherwise.
How to remove spyware
Spyware is a common problem for internet users. If you think your device has been infected, there are steps you can take to help remedy the problem.
From your computer
While it used to be more common on Windows, Mac spyware is increasingly becoming an issue. Mac spyware attacks have included stolen passwords and backdoors.
If you suspect your desktop or laptop computer has been infected with spyware, take these steps to identify the infection and remove it:
- Run a scan with your security software: The scan will help to identify and remove malware.
- Download and run a virus removal tool: A reputable virus removal tool scans for threats that traditional antivirus software may not detect.
Once you've cleaned your system, consider practicing prevention. There are high-quality anti-spyware tools available that will monitor your system continuously to help guard against spyware from accessing or modifying your personal information.
From your mobile phone
Mobile devices can become infected with spyware, too. If you've noticed any signs of mobile spyware, there are steps you can take to remove the spyware.
- Uninstall apps you don't recognise: Go to your phone's settings, click on "Apps," and uninstall any apps you find suspicious.
- Run an antivirus or malware scan: You may have an app that came packaged with your phone, or you may need to download and install a reputable app from the official app store for your device.
If uninstalling apps and running a malware scan doesn't fix the problem, consider backing up your data and then factory resetting your phone.
What to do after spyware removal
Your work isn't quite finished once the spyware has been removed from your device. There are some steps you should take to protect your personal data from being further exposed.
- Change your passwords: Once your system has been cleaned, take steps to secure your personal data by changing your email and other important account passwords.
- Alert your financial institutions: If you believe financial credentials such as credit card data may have been exposed, make sure your financial institution is on the lookout for fraudulent activity and keep an eye out for yourself.
Keeping your devices safe
Although not all spyware gains access to things like your passwords and credit card information, it can still make sense to safeguard important personal data after an infection.
With a better understanding of what spyware is and how it functions, you can take steps to keep your devices and your confidential data more secure.
Still concerned about potential hackers who want to access your data? Norton 360 Deluxe increases your chances of minimising threats. Not only does it help protect against cybercriminals accessing your information, but it also helps avoid suspicious behavior that can affect your device.
FAQ about spyware
Here are answers to a few of the most-asked questions about spyware.
Is spyware a virus?
Spyware and computer viruses are in the same family—they're both malicious types of software. But there are some differences. Spyware is a type of malware that collects your personal information and gathers data about you without your consent. Viruses are a type of malicious software designed to spread from your device to other devices.
Can spyware be detected?
Spyware can be detected by advanced internet security software and anti-malware software. If you've noticed that your computer or device is behaving differently (such as running slowly or displaying unusual or especially intrusive pop-ups), run a scan to identify and remove the threat.
What are examples of spyware?
Some of the most notorious spyware programmes that have been identified include:
- CoolWebSearch (CWS): This spyware has been around since 2003. It redirects your browser to a new homepage and then continuously creates pop-up ads, often to unsavory sites while changing browser permissions so that unsafe sites are marked "safe."
- Olympic Vision: Olympic Vision spreads through email campaigns aimed at employees of specific companies. It logs keystrokes and steals clipboard data and other user credentials.
- HawkEye: This keylogger covertly captures things like keystrokes, account credentials, and other high-risk personal information.
Are tracking cookies spyware?
Tracking cookies can be spyware, but it depends on the type of tracking cookie. Not all tracking cookies are harmful or disruptive.
First-party cookies aren't necessarily spyware. Reputable websites will ask you to accept their tracking cookies the first time you visit. These cookies help the website to identify you when you visit again and assist with things like login, accessing your user profile, and personalising your browsing experience while you're using the site.
Third-party cookies are often a type of spyware. They come from a website or ad server other than the site you're currently surfing, and they often allow advertisers to track your online activities or analytics companies to collect and sell your data.
What should I do if my device is infected?
If you believe your device is infected, isolate the device. Make sure to uninstall any suspicious apps or programmes. You’ll then want to use a spyware removal tool to scan for any threats and remove them.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips and updates.